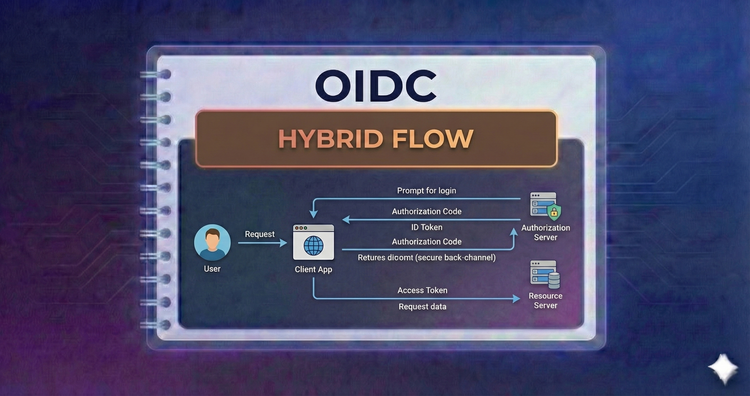
OIDC - Hybrid Flow
A mix of code and implicit flows. We’ll examine scenarios where you need an ID token immediately on the front end while still exchanging a code for long-lived access on the back end.
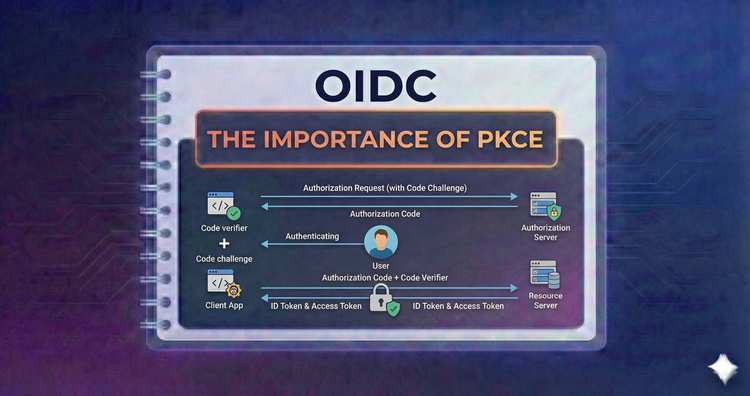
OIDC - The Importance of PKCE
Implicit flow is dead. Discover how Proof Key for Code Exchange secures public clients like mobile apps by cryptographically binding the authorization request to the exchange, preventing interception.
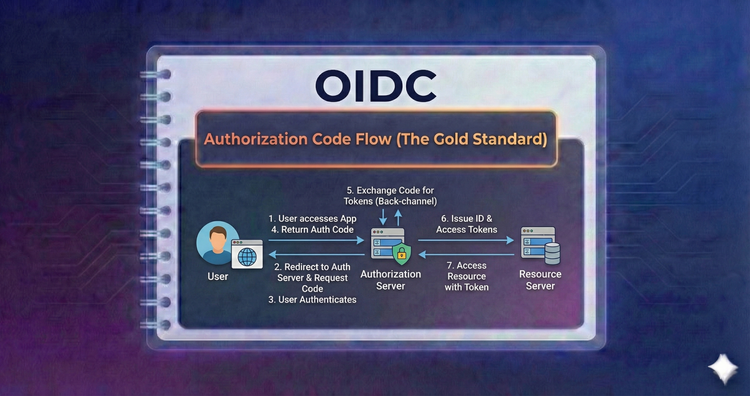
OIDC - Authorization Code Flow (The Gold Standard)
The most secure flow for server-side apps. We’ll walk through the exchange of an authorization code for tokens, ensuring sensitive tokens never touch the user’s browser or risk exposure.
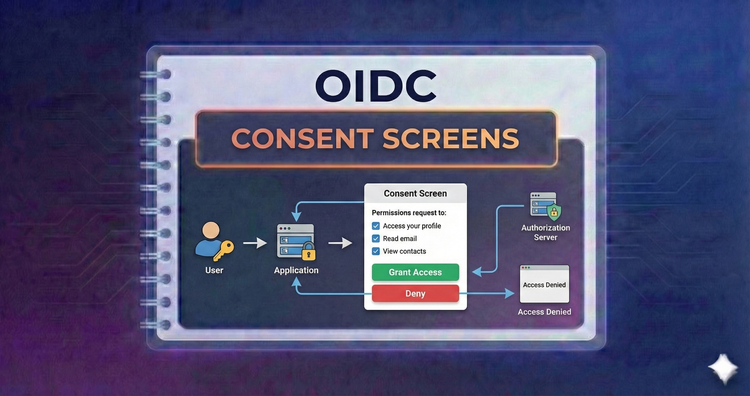
OIDC - Consent Screens
Trust is key. Learn how to design user-centric consent flows that clearly communicate what data is being requested, handling granular permissions while maintaining a smooth user experience.
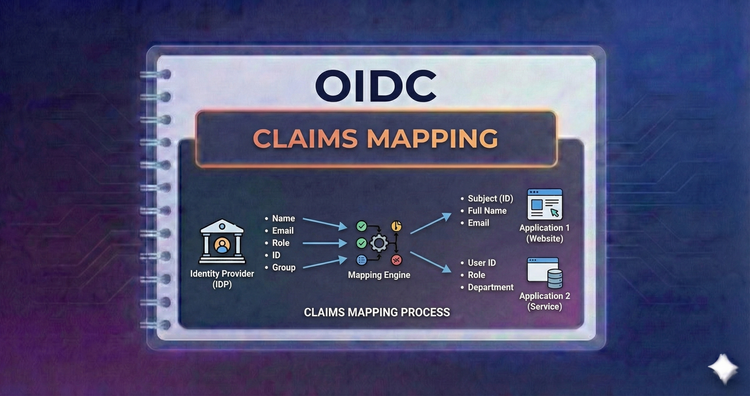
OIDC - Claims Mapping
How do scopes translate to data? We’ll map standard scopes to specific claims like name or picture and discuss how to inject custom data—like roles or subscription levels—into your tokens.
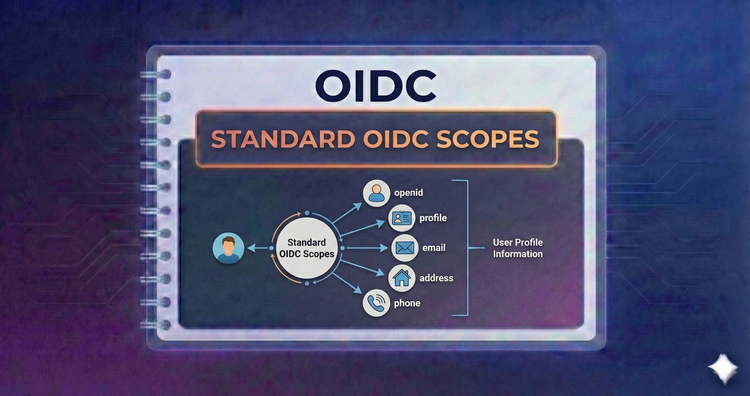
OIDC - Standard OIDC Scopes
Scopes define access boundaries. We’ll cover the mandatory openid scope and optional ones like profile, email, and offline_access that control exactly what user data your application requests.
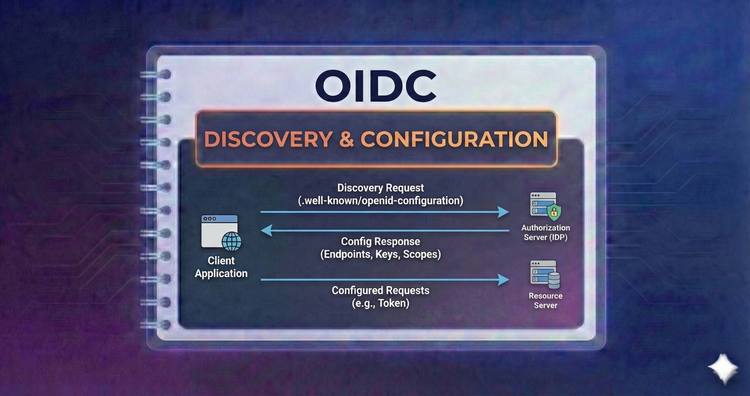
OIDC - Discovery & Configuration
Stop hardcoding endpoints. We’ll explore the .well-known configuration document, enabling your applications to automatically discover issuer URLs, keys, and supported scopes for seamless setup.
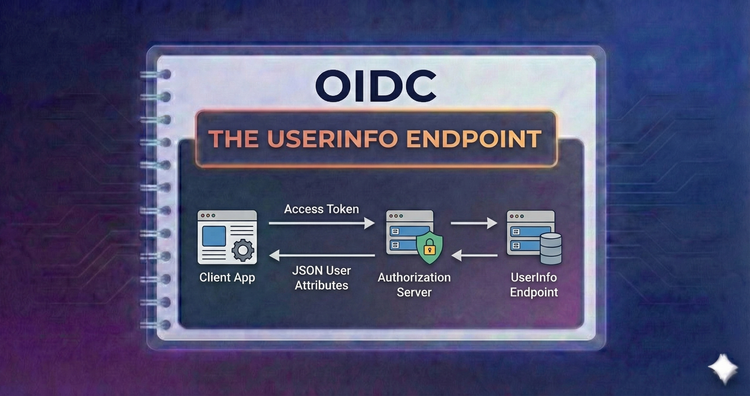
OIDC - The UserInfo Endpoint
Sometimes the ID Token isn't enough. Learn how to query this protected resource to fetch extended user attributes, balancing the trade-off between token size and additional API network calls.
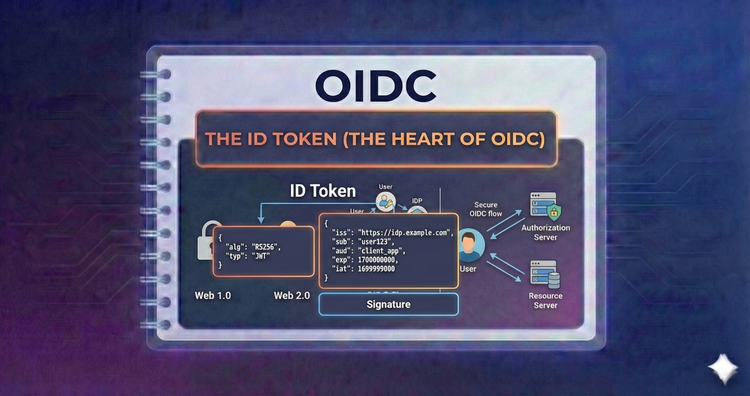
OIDC - The ID Token (The Heart of OIDC)
Meet the JWT-based token that distinguishes OIDC from standard OAuth. We’ll dissect its structure—Header, Payload, Signature—and examine key claims like sub, iss, and exp that prove a user's identity.
OIDC - What is OIDC?
OpenID Connect adds an intelligent identity layer on top of OAuth 2.0. Learn how it standardizes Single Sign-On (SSO) and allows apps to verify user identity securely without managing passwords directly.