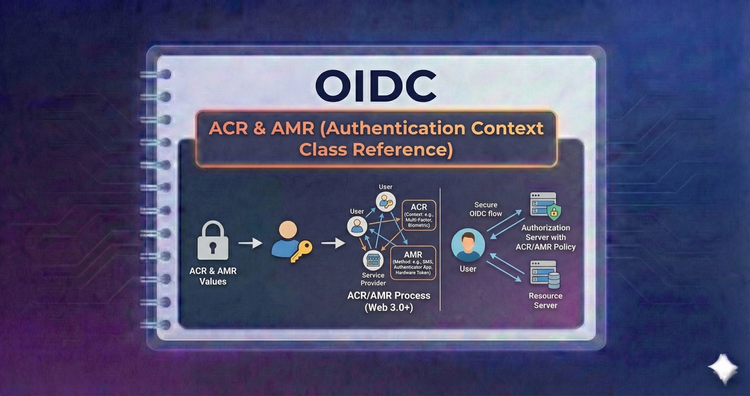
OIDC - ACR & AMR (Authentication Context Class Reference)
Not all logins are equal. Use these values to demand higher security standards—like forcing Multi-Factor Authentication (MFA)—or to audit exactly how a user authenticated (e.g., password vs. bio).
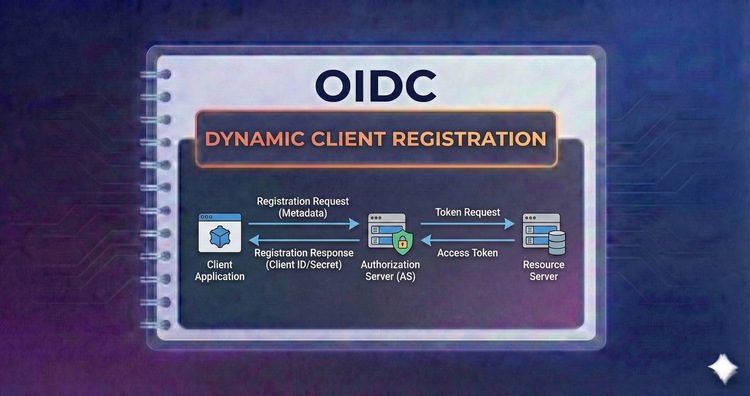
OIDC - Dynamic Client Registration
Move beyond manual setup. Learn how Relying Parties can programmatically register with OpenID Providers, automating the exchange of client IDs and secrets for scalable, multi-tenant architectures.
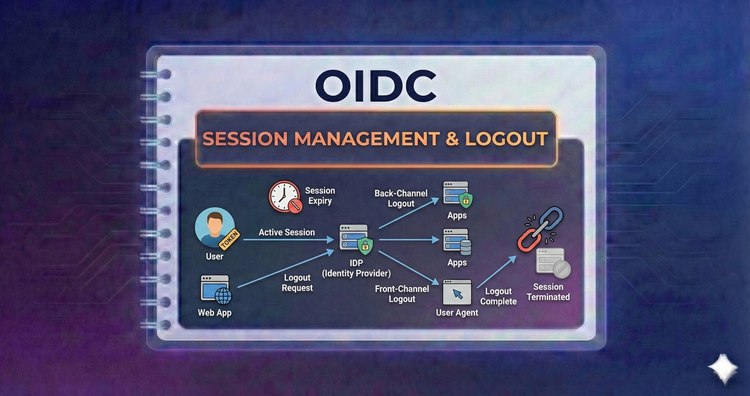
OIDC - Session Management & Logout
Logging in is easy; logging out is hard. We’ll tackle Single Logout (SLO), distinguishing between front-channel and back-channel mechanisms to ensure sessions are terminated cleanly across all apps.
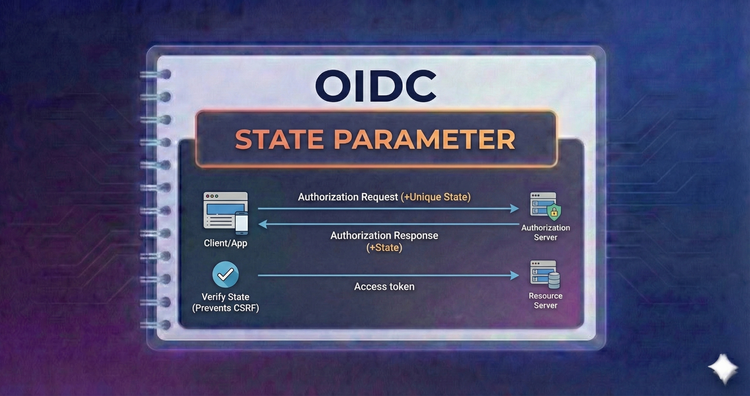
OIDC - State Parameter
Defend against Cross-Site Request Forgery (CSRF). We’ll use the state parameter to cryptographically bind the request to the callback, ensuring the response you receive is actually the one you asked for.
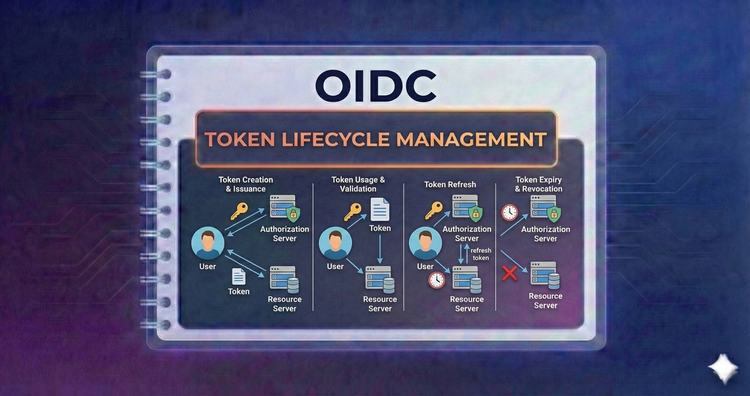
OIDC - Token Lifecycle Management
Tokens expire for a reason. Master the dance of short-lived access tokens and long-lived refresh tokens, including strategies for rotation and revocation to maintain security without annoying users.
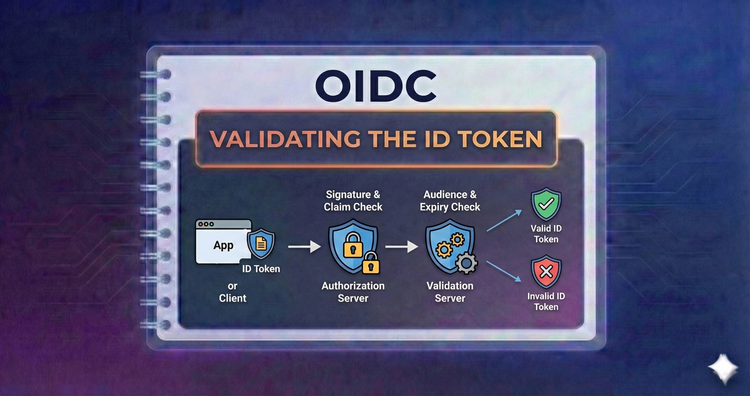
OIDC - Validating the ID Token
Trust, but verify. We’ll implement rigorous checks for signatures (RS256), audiences (aud), and issuers (iss) to ensure incoming tokens are authentic and haven't been tampered with.
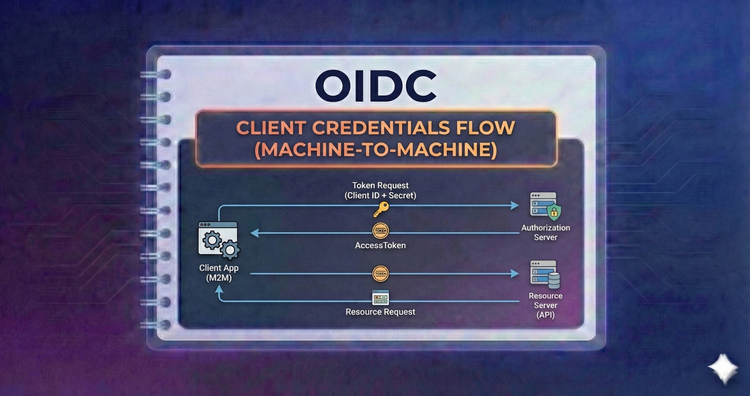
OIDC - Client Credentials Flow (Machine-to-Machine)
Not all users are humans. Learn how services and daemons authenticate with each other using OIDC principles, securing server-to-server communication without user interaction or UI.
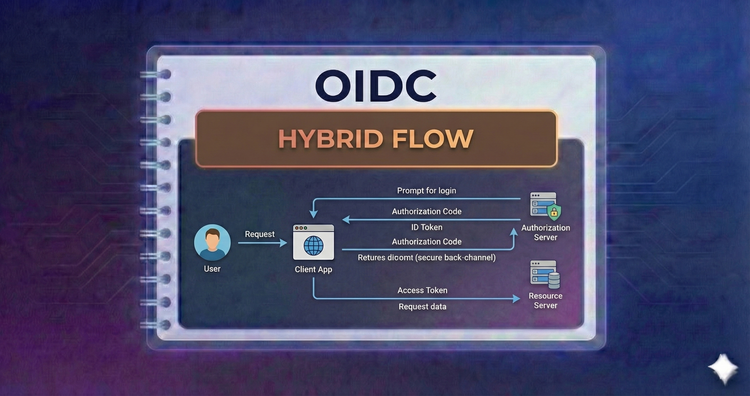
OIDC - Hybrid Flow
A mix of code and implicit flows. We’ll examine scenarios where you need an ID token immediately on the front end while still exchanging a code for long-lived access on the back end.
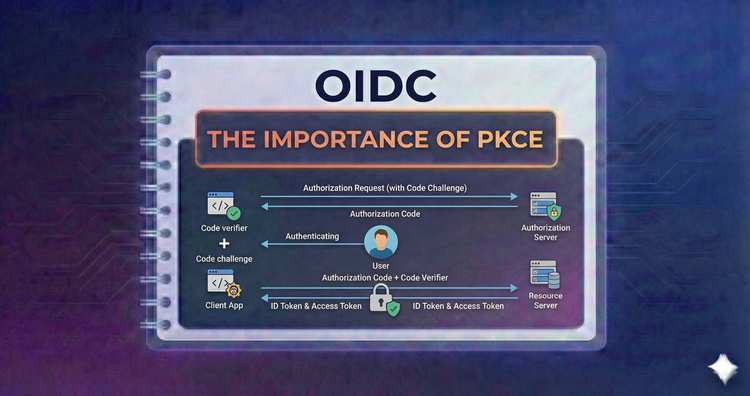
OIDC - The Importance of PKCE
Implicit flow is dead. Discover how Proof Key for Code Exchange secures public clients like mobile apps by cryptographically binding the authorization request to the exchange, preventing interception.
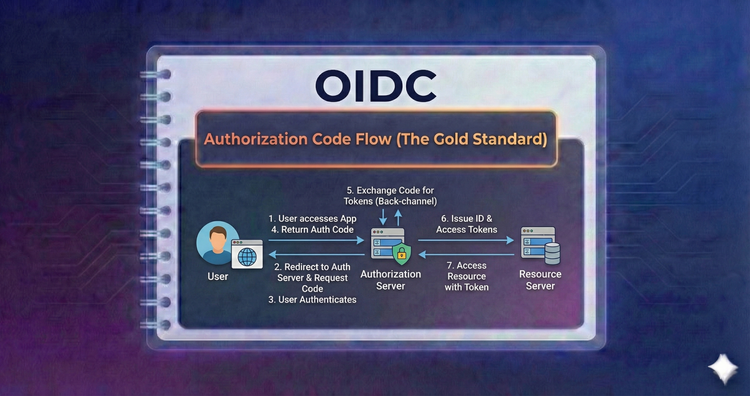
OIDC - Authorization Code Flow (The Gold Standard)
The most secure flow for server-side apps. We’ll walk through the exchange of an authorization code for tokens, ensuring sensitive tokens never touch the user’s browser or risk exposure.